Why Is A Common Protocol Suite Necessary For Transmission Of Data Over Remote Networks?
12 common network protocols and their functions explained
Networking makes the internet piece of work, but neither tin succeed without protocols. Common network protocols and functions are key for communication and connection across the internet.
Without network protocols, the mod net would stop to exist.
Common network protocols, including Transmission Control Protocol (TCP) and Internet Protocol (IP), enable the exchange of information across the internet and work backside the scenes so effectively that many users don't think twice about them or how the internet works. For networking professionals, network protocols are critical to know and understand. But that doesn't make understanding these protocols easy.
To get started, this glossary explores 12 common network protocols all network engineers should exist familiar with. This includes the protocols' primary functions, also every bit why these common network protocols are important.
12 common network protocols explained
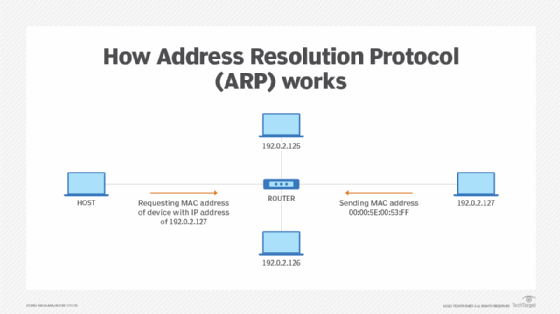
Address Resolution Protocol . ARP translates IP addresses to Media Admission Control (MAC) addresses and vice versa and then LAN endpoints tin communicate with one another. ARP is necessary because IP and MAC addresses are different lengths: IP version 4 (IPv4) addresses are 32 bits long, IPv6 addresses are 128 bits and MAC addresses -- a device'southward concrete hardware number -- are 12 hexadecimal digits split into six pairs. Translations must occur for proper device advice.
ARP isn't required every time devices attempt to communicate because the LAN's host stores the translated addresses in its ARP enshroud, so this process is mainly used when new devices join the network.
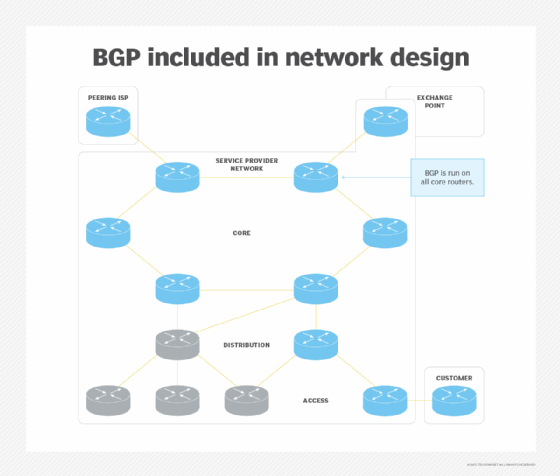
Border Gateway Protocol . BGP makes the internet piece of work. This routing protocol controls how packets laissez passer through routers in an democratic system (Equally) -- ane or multiple networks run by a unmarried organization or provider -- and connect to different networks. BGP tin can connect endpoints on a LAN to one another, and information technology can connect endpoints in different LANs to one some other over the internet.
External BGP directs network traffic from various ASes to the internet and vice versa. Additionally, internal BGP directs network traffic between endpoints within a unmarried Every bit.
Domain name system . DNS is a database that includes a website's domain proper name, which people use to admission the website, and its corresponding IP addresses, which devices use to locate the website. DNS translates the domain name into IP addresses, and these translations are included within the DNS. Servers can cache DNS data, which is required to access the websites. DNS besides includes the DNS protocol, which is within the IP suite and details the specifications DNS uses to translate and communicate.
DNS is of import because it tin quickly provide users with data, as well equally access to remote hosts and resource across the net.
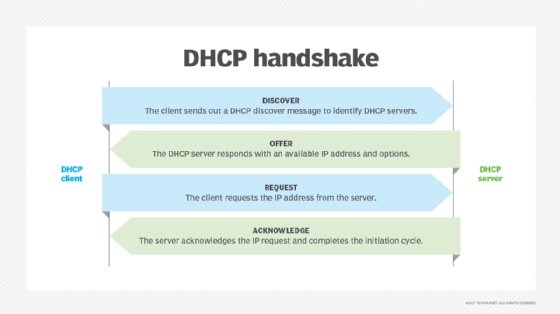
Dynamic Host Configuration Protocol . DHCP assigns IP addresses to network endpoints and then they tin can communicate with other network endpoints over IP. Whenever a device joins a network with a DHCP server for the first time, DHCP automatically assigns information technology a new IP address and continues to do and then each fourth dimension a device moves locations on the network.
When a device connects to a network, a DHCP handshake takes place, where the device and DHCP server communicate. The device establishes a connection; the server receives it and provides available IP addresses; the device requests an IP accost; and the server confirms information technology to complete the process.
File Transfer Protocol . FTP is a customer-server protocol, with which a client requests a file and the server supplies information technology. FTP runs over TCP/IP -- a suite of communications protocols -- and requires a command channel and a data channel to communicate and substitution files, respectively. Clients asking files through the command channel and receive access to download, edit and copy the file, among other deportment, through the information channel.
FTP has grown less popular as most systems began to use HTTP for file sharing. However, FTP is a mutual network protocol for more private file sharing, such as in cyberbanking.
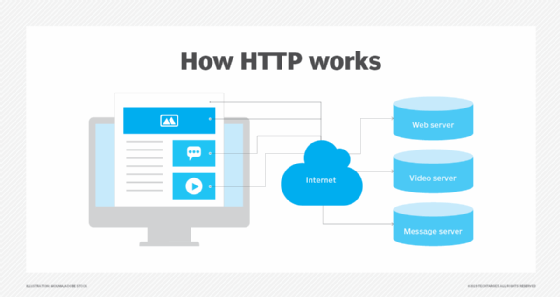
Hypertext Transfer Protocol . Like FTP, HTTP is a file sharing protocol that runs over TCP/IP, although HTTP primarily works over web browsers and is ordinarily recognizable for most users. When a user enters a website domain and aims to access it, HTTP provides the access. HTTP connects to the domain's server and requests the site's HTML, which is the code that structures and displays the page's design.
Another form of HTTP is HTTPS, which stands for HTTP over Secure Sockets Layer or HTTP Secure. HTTPS tin encrypt a user's HTTP requests and webpages. This provides more security to users and tin can forestall mutual cybersecurity threats, such as man-in-the-middle attacks.
Net Protocol . IP functions similarly to a postal service. When users send and receive data from their device, the data gets spliced into packets, which are like letters with 2 IP addresses: one for the sender and 1 for the recipient. After the packet leaves the sender, it goes to a gateway, like a postal service office, that directs it in the proper direction. Packets go on to travel through gateways until they accomplish their destinations.
IP is commonly paired with TCP to form TCP/IP, the overall internet protocol suite. Together, IP sends packets to their destinations, and TCP arranges the packets in the correct order, as IP sometimes sends packets out of order to ensure the packets travel the fastest ways.
Open Shortest Path First . OSPF works with IP in sending packets to their destinations. IP aims to send packets on the quickest route possible, which OSPF is designed to attain. OSPF opens the shortest, or quickest, path first for packets. Information technology as well updates routing tables -- a set of rules that command where packets travel -- and alerts routers of changes to the routing table or network when a change occurs.
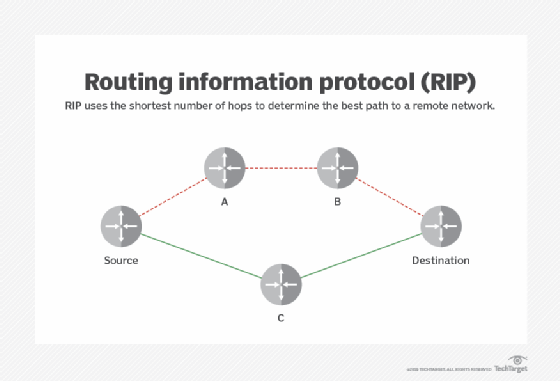
OSPF is similar to and supports Routing Information Protocol -- which directs traffic based on the number of hops it must accept along a route -- and it has also replaced RIP in many networks. OSPF was adult every bit a more streamlined and scalable alternative to RIP. For instance, RIP sends updated routing tables out every 30 seconds, while OSPF sends updates only when necessary and makes updates to the detail part of the table where the change occurred.
Simple Mail Transfer Protocol . SMTP is the most popular email protocol, is part of the TCP/IP suite and controls how electronic mail clients send users' e-mail messages. Email servers utilise SMTP to send email messages from the client to the email server to the receiving email server. Withal, SMTP doesn't control how email clients receive messages -- just how clients send letters.
That said, SMTP requires other protocols to ensure email messages are sent and received properly. SMTP can work with Post Office Protocol 3 or Internet Bulletin Access Protocol, which control how an electronic mail server receives email messages.
Telnet . Telnet is designed for remote connectivity, and it establishes connections betwixt a remote endpoint and a host machine to enable a remote session. Telnet prompts the user at the remote endpoint to log on and, in one case authenticated, gives the endpoint admission to network resource and data at the host estimator.
Telnet has existed since the 1960s and was arguably the offset typhoon of the mod net. Still, Telnet lacks sophisticated security protections required for modernistic communications and technology, so information technology isn't normally used anymore.
Transmission Control Protocol . TCP is the other one-half of TCP/IP and arranges packets in lodge so IP can evangelize them. Specifically, TCP numbers private packets because IP tin can send packets to their destinations through different routes and get them out of order, so TCP amends this before IP delivers the packets.
TCP likewise detects errors in the sending process -- including if whatsoever packets are missing based on TCP's numbered system -- and requires IP to retransmit those packets earlier IP delivers the information to its destination. Through this process, the TCP/IP suite controls communication beyond the internet.
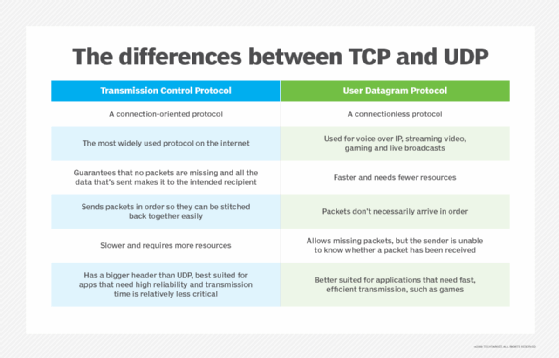
User Datagram Protocol . UDP is an alternative to TCP and also works with IP to transmit time-sensitive data. UDP enables low-latency data transmissions between cyberspace applications, and so this protocol is ideal for voice over IP or other audio and video requirements. Dissimilar TCP, UDP doesn't wait for all packets to arrive or organize the packets. Instead, UDP transmits all packets even if some haven't arrived.
UDP solely transmits packets, while TCP transmits, organizes and ensures the packets arrive. While UDP works more speedily than TCP, it'south also less reliable.
This was last published in Baronial 2020
Dig Deeper on Network protocols and standards
-

BGP (Border Gateway Protocol)
-

User Datagram Protocol (UDP)
-

Transmission Command Protocol (TCP)
-

ping sweep (ICMP sweep)
Why Is A Common Protocol Suite Necessary For Transmission Of Data Over Remote Networks?,
Source: https://www.techtarget.com/searchnetworking/feature/12-common-network-protocols-and-their-functions-explained
Posted by: hodginwitswoompose1968.blogspot.com






0 Response to "Why Is A Common Protocol Suite Necessary For Transmission Of Data Over Remote Networks?"
Post a Comment